漏洞修复-Nginx-SSLTLS-弱密码套件

目录
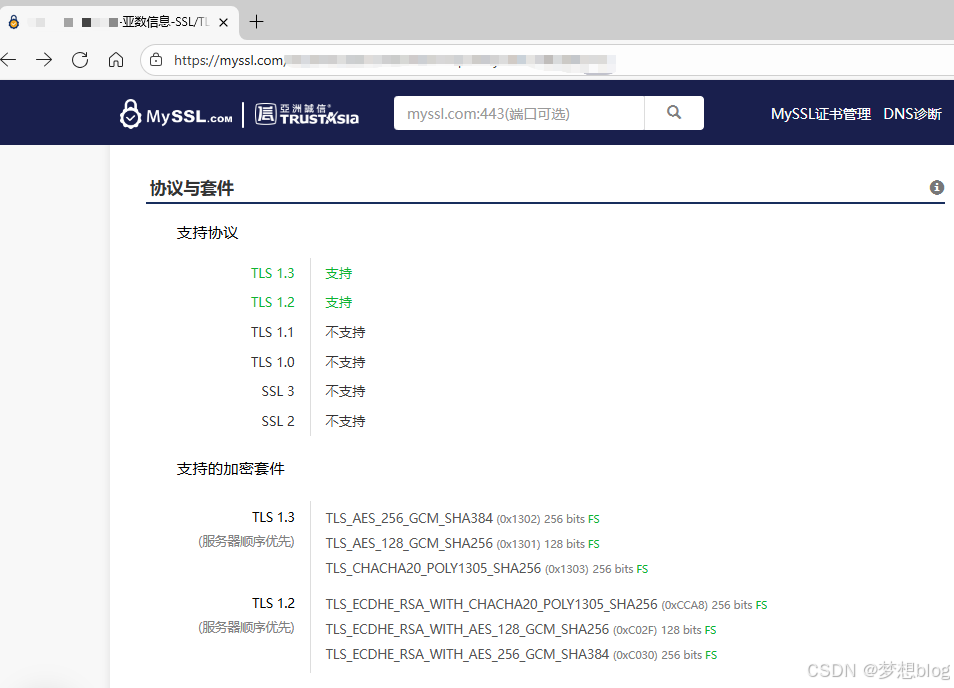
漏洞修复 Nginx SSL/TLS 弱密码套件
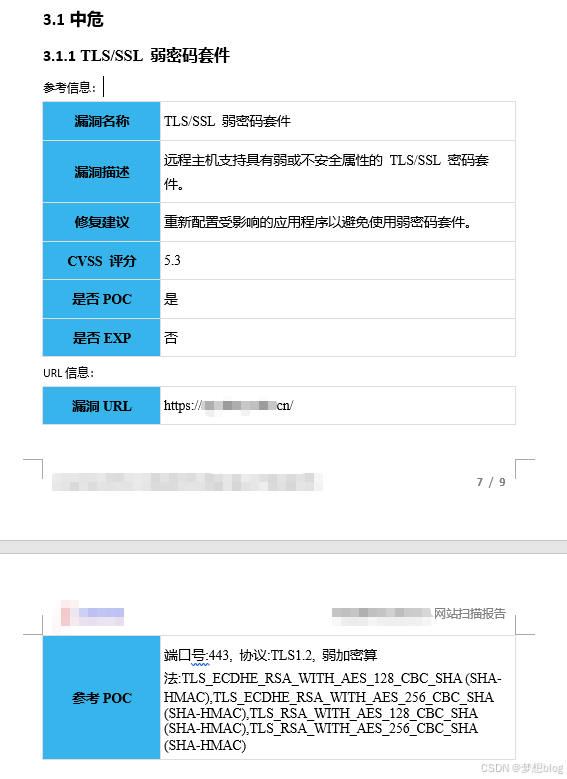
扫描结果
[root@localhost nmap]# docker run --rm -v $(pwd)/results:/results securecodebox/nmap nmap --script ssl-enum-ciphers -p 443 xxx.cn -oX /results/output_0904.xml
Starting Nmap 7.80 ( https://nmap.org ) at 2025-09-04 05:02 UTC
Nmap scan report for xxx.cn (ip)
Host is up (0.019s latency).
Other addresses for xxx.cn (not scanned): ip
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (ecdh_x25519) - A
| TLS_RSA_WITH_AES_128_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA256 (rsa 2048) - A
| TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A
| TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A
| compressors:
| NULL
| cipher preference: server
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 2.91 seconds解决,先在测试环境试试
修改配置前,测试
[root@localhost nmap]# docker run --rm -v $(pwd)/results:/results securecodebox/nmap nmap --script ssl-enum-ciphers -p 5173 test_ip -oX /results/output_21_test.xml
Starting Nmap 7.80 ( https://nmap.org ) at 2025-09-04 05:06 UTC
Nmap scan report for test_ip
Host is up (0.00096s latency).
PORT STATE SERVICE
5173/tcp open unknown
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| compressors:
| NULL
| cipher preference: server
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 0.47 secondsNginx 配置修改前
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256';Nginx 配置修改后
ssl_prefer_server_ciphers on;
ssl_protocols TLSv1.3;Nginx 修改配置后,测试
[root@localhost nmap]# docker run --rm -v $(pwd)/results:/results securecodebox/nmap nmap --script ssl-enum-ciphers -p 5173 test_ip -oX /results/output_21_test.xml
Starting Nmap 7.80 ( https://nmap.org ) at 2025-09-04 05:07 UTC
Nmap scan report for test_ip
Host is up (0.00048s latency).
PORT STATE SERVICE
5173/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 0.44 seconds生产环境复扫,还是存在问题
原因:应该是外面还包了一层导致的,应该是服务商的云防护之类的东西,我们修复也没有用。
结论
测试环境还是修复完成了。
生产环境让提供网关的服务商修复即可。
后续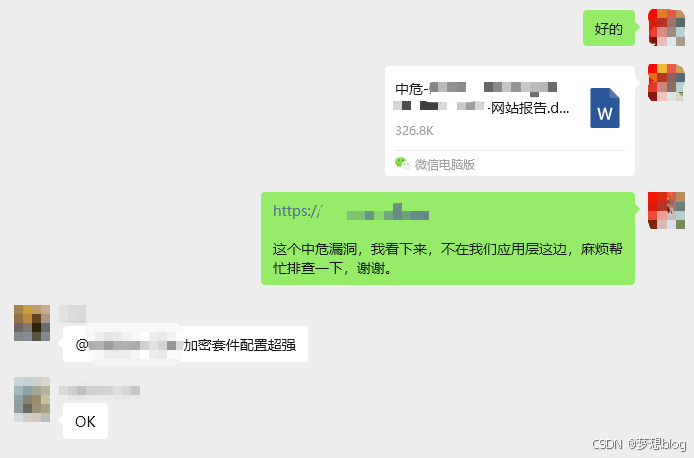
复扫
[root@localhost nmap]# docker run --rm -v $(pwd)/results:/results securecodebox/nmap nmap --script ssl-enum-ciphers -p 443 test.cn -oX /results/output_0904.xml
Starting Nmap 7.80 ( https://nmap.org ) at 2025-09-04 06:29 UTC
Nmap scan report for test.cn (ip)
Host is up (0.020s latency).
Other addresses for test.cn (not scanned): 112.84.222.49
PORT STATE SERVICE
443/tcp open https
| ssl-enum-ciphers:
| TLSv1.2:
| ciphers:
| TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (ecdh_x25519) - A
| TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (ecdh_x25519) - A
| compressors:
| NULL
| cipher preference: server
|_ least strength: A
Nmap done: 1 IP address (1 host up) scanned in 14.57 seconds在线验证